
Hijacking bluetooth headsets
Press and hold the Bluetooth button and Power button for up to fifteen seconds. (In some cases the device will not have a Bluetooth button, instead hold the Volume Up and Power buttons for fifteen seconds.) The device should power cycle and turn on in pairing mode. Quickly pair with the speaker before the signal pirate does.
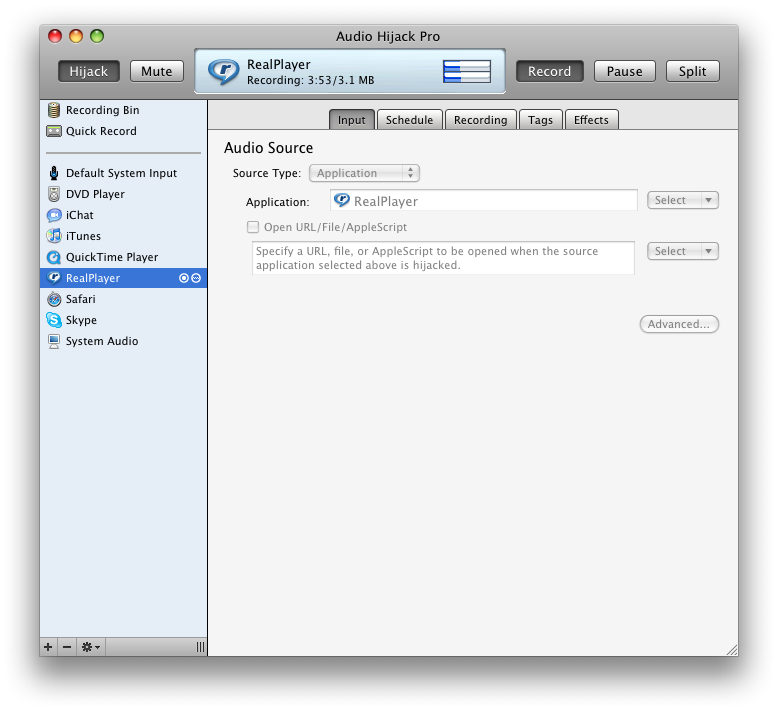
Audio Hijack Pro 3 2 0 for Macintosh OS X
A low-power standby mode to monitor press of the power button. Protecting battery from over-discharge. A voltage regulator supplying battery power to the device. An audio line-in jack. Volume.

Hijacking bluetooth headsets
You need a Cheap CB radio, A linear amp, and a bottom loaded CB antenna (easier to build a ground plane for it). See if you can get a good guess where she has her [speakers] set up and get your.
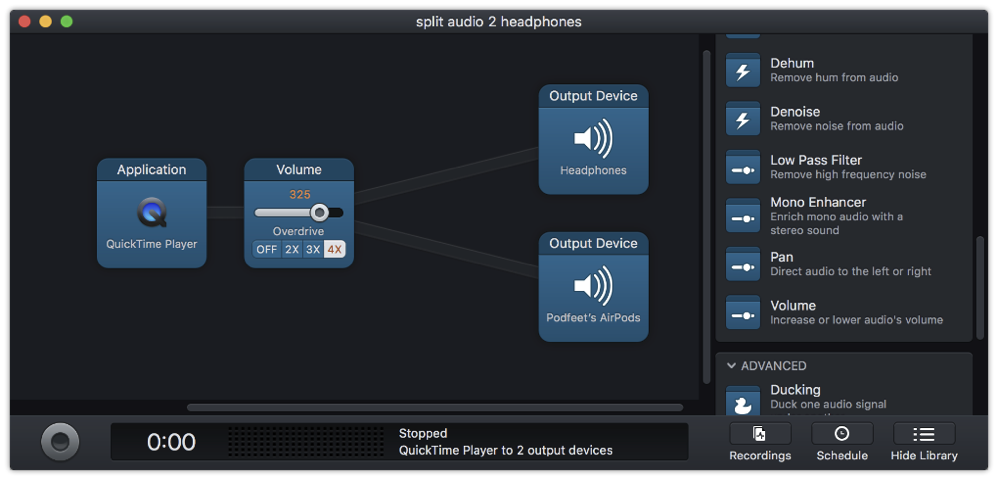
Solving Airplane Noise Problems with Audio Hijack Podfeet Podcasts
Go to Settings, then click Bluetooth on the device you want to connect (for example, your phone) and look for your speaker in the list of Bluetooth devices. To connect, turn ON the Bluetooth speaker. After pressing the connect button, turn the speaker ON while your device tries to connect to it.

iPhone headset socket hijacked to power DIY peripherals video
Swipe down from the top of the screen to bring down the Notification menu, then tap the “Bluetooth” icon in the resulting drop-down. If the “Bluetooth” icon is highlighted or blue, it’s already on. You may have to turn on Bluetooth for the other phone as well. 4 Connect to the phone you want to hack.
EXCLUSIVE How to hack bluetooth speaker
Way 1 – Be the First One to Pair Up The easiest way to connect to your speaker is by being the first one to pair up. This lets you have full control over the device. Most of the speakers have a built-in default PIN. But if a speaker lacks this default PIN, it is easy to hijack it. Way 2 – Use the Efficient KNOB Attack
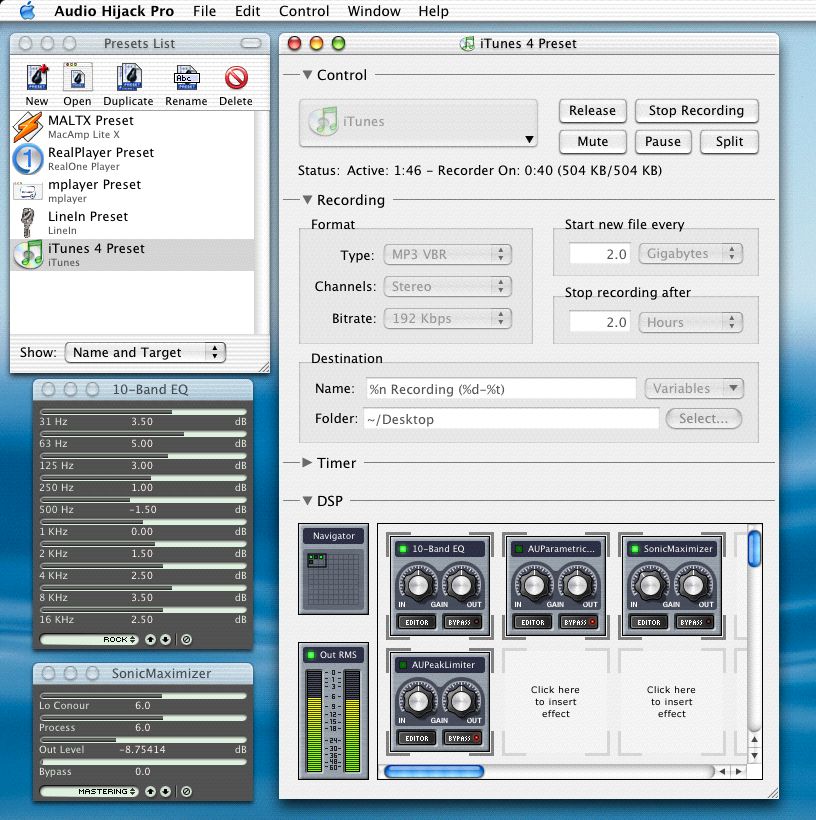
Good Freeware Blog AUDIO HIJACK DOWNLOAD
A lot of speakers are pairable when they’re not streaming music but still on. Get close, look for Bluetooth devices and see if you can just pair with them. The thing about hijacking is that once someone is connected, you just take over the thing. I think this is op point.

Hijacking bluetooth headsets
In a controlled environment, we were able to leverage our access to the decrypted link and hijack the Bluetooth session. Setting up the Man in the Middle We were able to escalate the attack by setting up a relay for MitM after using KNOB to crack the link encryption.

Hijacking bluetooth headsets
You can hijack a Bluetooth speaker by first doing KNOB. With KNOB opening the door, do not stop there with your attack. Take it one step further and try to hijack the Bluetooth session in a controlled environment by using the decrypted link you have. Set Up A Man In The Middle Attack Use the KNOB to break the link.
Bluetooth Comparitech New Place
Strangers connecting to your Bluetooth speakers? Input jack getting overridden by unknown Bluetooth connections? I show how I stopped it on Klipsch ProMedi.

Hijacking bluetooth headsets
The LINK-KEY being the pairing key that is used to authenticate devices with each other. This would also require passive sniffing then using BTCrack to break it. Try to utilize your bluetooth with the programs that come with Kali and if you’re able to use it look at the resources that u/mylifeinbinary010101 suggested.

Hijacking bluetooth headsets
This type of cyber attack involves one Bluetooth-enabled device hijacking another and sending spam messages to the hijacked device.. Furthermore, smart devices such as fitness trackers or Bluetooth speakers that use Bluetooth to communicate with mobile apps can be hacked and the attacker can “listen in” or collect data.

The flexibility of Audio Hijack 3 Six Colors
Identify Susceptible Devices. The first step in hijacking a Bluetooth speaker is to identify susceptible devices. This involves scanning the area for any Bluetooth enabled devices that are not properly secured. To do this, attackers can use specialized tools such as Bluetooth scanners or wireless sniffers. These tools can be used to detect any.

Speakers With Everything Except the Sticker Shock Wireless speakers
Thank you for watching I hope you enjoyed. Please kindly subcribe to the Channel so that you will be notified on our next episode.Download the song here : ht.

How To Hack Bluetooth Speaker App
The Risks Involved in Hijacking a Bluetooth Speaker When hijacking a bluetooth speaker, there are several risks involved. First and foremost, there is the risk of compromising your personal information or data stored on the device. If an attacker gains access to your device, they could potentially steal sensitive information such as passwords.
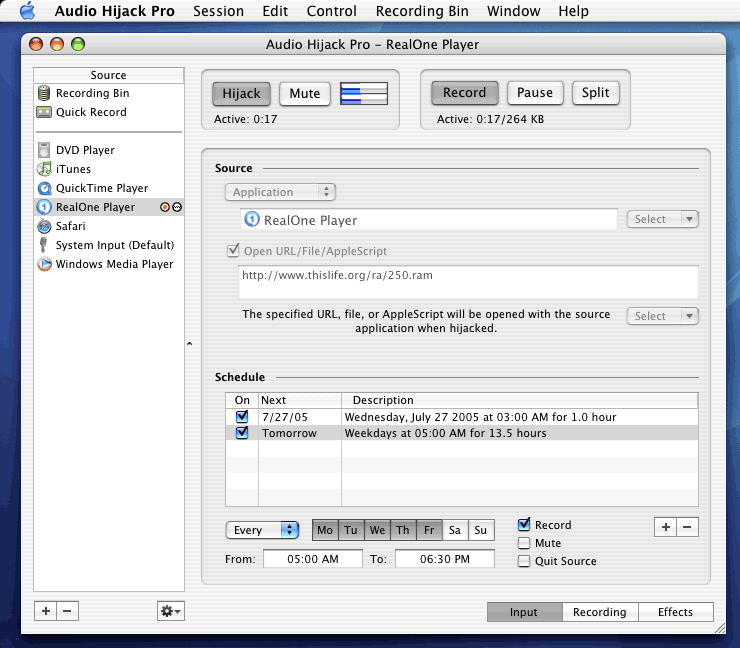
Audio Hijack Pro Download
Have a Security Code. Many modern devices are equipped with advanced security features, which restrict Bluetooth pairing. These speakers when paired with any other device, be it a smartphone or other speakers in the household, provide a code. In that case, anyone who wants to access your speaker will have to know this code.